The quantity of Mac viruses is growing at an alarming rate and solid protection against these threats is essential if you wish to prevent identity theft, file corruption or interception of your credit card details. Comodo Antivirus provides the state-of-the-art virus protection to your Mac OS computer at no cost. Aug 11, 2020 Well-respected malware protection vendor Malwarebytes reports they saw more malware on Mac machines in 2017 than in any previous year. How to find out if your Mac was infected Malware can take many forms on Mac, but perhaps the most popular forms of malware today are adware and illicit cryptocurrency mining.
- What Is Malware Browser Guard
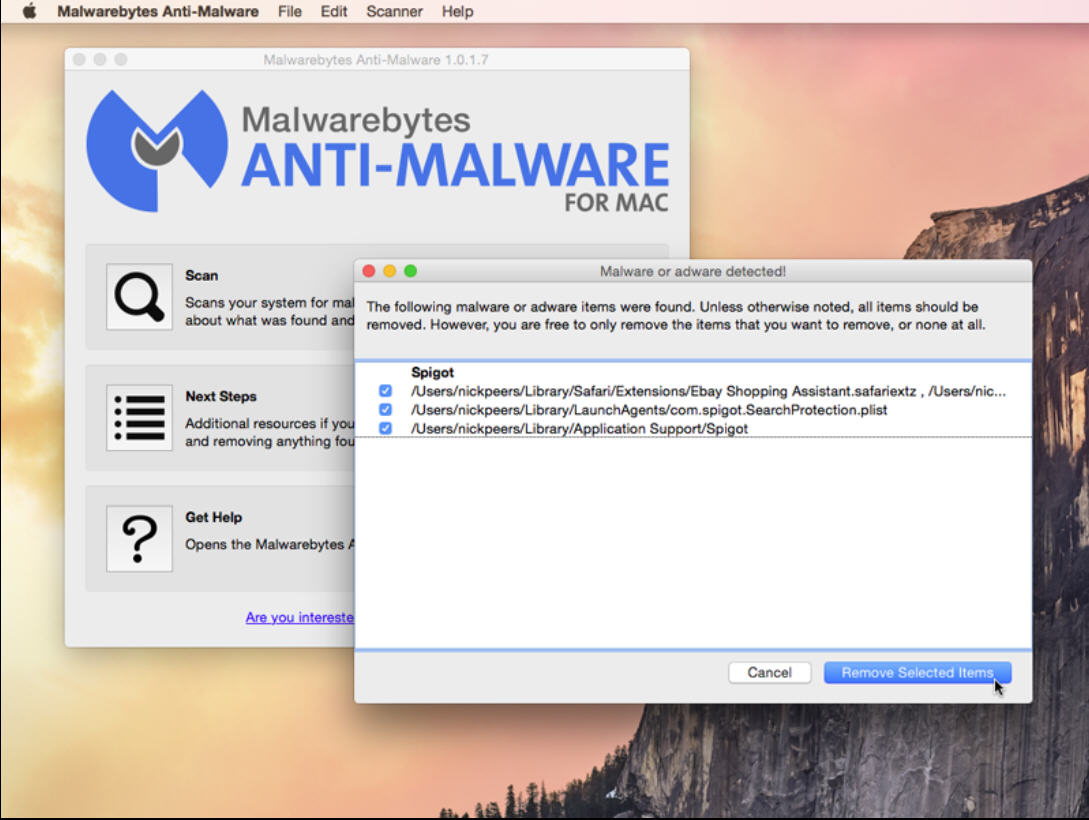
- Anti Malware Mac
- Guard Your Mac Against Malware Windows 10
- Guard Your Mac Against Malware Threats
Can Macs get viruses?
In addition to their ability to work seamlessly with Apple devices, many users prefer Mac computers because of their perceived 'inherent' security features. Apple also notifies users of periodic updates to make sure that every generation of Apple product has the most secure software version. And while Apple does go to great lengths to keep its devices safe by making it difficult to download any/all software foreign to its official Apple application store, this does NOT mean your Mac is immune to all computer viruses.
What is a virus?
A virus is any piece of malicious software that invades your computer system, then copies itself. They can also then spread to other systems. This could result in stolen personal information or financial data, corrupted files, or crypto-hijacking. Here are some of the common viruses that infect Apple devices, and some of the best ways to protect your computer from them.
CookieMiner
CookieMiner is malware that captures Chrome browser authentication cookies primarily associated with cryptocurrency exchanges. The sophisticated CookieMiner code bypasses strict security protocols of both Apple and cryptocurrency exchanges by stealing information such as passwords, usernames, and other login credential data. It can even capture backed-up data from iTunes accounts that can be used to open cryptocurrency wallets and then steal cryptocurrencies such as Bitcoin, Ethereum, and XRP. Stealing valuable cryptocurrency isn't enough for CookieMiner hackers, however, as they also use this malware to load cryptocurrency mining software onto MacBooks to mine Koto, a little-known Japanese cryptocurrency.
Besides a significantly lighter cyber wallet, there are some other clues that your Mac may be infected by the CookieMiner virus. As a cryptocurrency miner, CookieMiner uses a significant amount of a CPU's processing power and therefore, infected Macs will be slow to complete even basic computing tasks. You may also notice that other software applications on your Mac don't work as well as they should or stop working completely, or tour Mac could also overheat.
OSX/Dok… Next Generation
OSX/Dok is malware that commandeers data traffic entering and leaving a Mac computer without your knowledge. It reroutes this traffic through a bogus proxy server to then obtain access to all your communications. The malware is able to counter Apple's security because it's signed by a legitimate developer certificate that validates its authenticity. Through OSX/Dok, a hacker even has access to data that moves through SSL-TLS encrypted connections such as banking information. This is especially troubling since Apple devices such as iPhones, iPads, and MacBooks are commonly synced to operate together.
While the original version of OSX/Dok was thwarted when Apple disabled its associated developer certificate, later versions have popped up using different developer certificates. Apple devices are vulnerable to this malware mainly when users are duped to download files through email phishing scams. Once the software is installed on your computer, it immediately takes over critical operations. Users then most often see a message that the system has detected a security issue. The malware prompts users to install an update, and it then locks up all operations until the user submits a password to install it. After obtaining the password, the malware then has full administrative privileges to take control of the device.
Crossrider
Crossrider is a variant on the OSX/Shlayer malware and uses a fake Adobe Flash player installer to dump other pieces of malicious code onto your Apple devices. Users mistakenly download the fake installer when they're sent a message to update Adobe Flash player. If you follow the link, you'll mistakenly download the fake installer instead of the real update from the Adobe website. The fake installer message will then prompt you to submit your password so that the software can make changes to your system and install the program.
Advanced Mac Cleaner, Chumsearch Safari Extension, and MyShopCoupon+ are some of the items that are installed through the fake Adobe Flash player installer. While MyShopCoupon+ and Chumsearch Safari Extension do cause minor annoyances to users, Advanced Mac Cleaner can cost you much more if you're not careful. Advanced Mac Cleaner appears to run a security scan of your system and identifies several issues. It then asks the user to pay $107 to activate the program's clean-up feature.
Macros Viruses… From Microsoft Word
Macro viruses used to be a problem that only PC users face. Macros are pieces of code that programmers embed within applications to automate routine tasks. The code, which is written in Visual Basic, can be used to hijack applications and do harm when users open popular Microsoft Office products such as Word, Excel, or Project. Visual Basic commands in macros can result in deleted or corrupted files. When you use Word to open an infected file, Word catches the virus and passes it on to every Word document that you subsequently create.
Apple disabled macro support in its early versions of Office for Mac, but it recently allowed macros to be supported in its later versions of both Word and Excel. But Mac users still have some protection against macros viruses since Apple doesn't allow macros to be automatically enabled by default.
MShelper
MShelper is a cryptocurrency mining malware that allows a hacker to help himself to your computer's processing capabilities in order to steal cryptocurrency. Hackers also develop this malware to display advertisements on the screens of popular browsers such as Mozilla, Chrome, and Firefox. Cybersecurity experts contend that MShelper infects computers when users download files of dubious origins. Some signs that your computer has been infected by MShelper include lowered battery life, fast-spinning fans, overheating, and increased noise.
Since crypto mining software takes a great deal of CPU power, it's not hard to spot if MShelper is on your Mac. Click on the CPU tab under Activity Monitor on your computer. If MShelper has infected your MacBook, it'll show up at the top of the list of applications with an extremely high CPU usage.
OSX/MaMi
OSX/MaMi is malware that allows hackers to capture sensitive information by redirecting data traffic through malicious servers. Through OSX/MaMi, hackers hijack Domain Name System (DNS) servers and change the DNS settings on your Mac. This malware allows attackers to perform many harmful tasks such as stealing login credentials, uploading and downloading files, and spying on your internet traffic.
What Is Malware Browser Guard
While OSX/MaMi is nearly undetectable, experts say that it's not yet been used to target Mac users on a widespread basis. Victims of this malware encounter it through targeted email phishing scams. A sign that your Mac has been infected by OSX/MaMi is a change in its DNS settings. A MacBook infected with this malware often shows these two addresses: 82.163.143.135 and 82.163.142.137.
Tips for Safeguarding Macs Against Malware
While Apple does an amazing job of guarding Macs against common security threats, it just can't stop every determined hacker who looks at its devices as a challenge.
Here are some top tips for shoring up security for your Mac:
- Avoid opening spam emails and attachments.
- Don't download questionable files.
- Install ad-blocking applications.
- Create frequent system backups (Time Machine).
- Install the latest OS and application updates.
- Manage data.
- Install a security suite (Antivirus, firewall, browser destination monitoring).
- User VPN software when connected to public or untrusted networks.
Stay protected
Subscribing to a comprehensive security suite service is one of the most effective steps that you can take to safeguard your Apple devices, financial information, and privacy while online. McAfee partners with industry, IT experts, and the user community to deliver the most powerful cybersecurity solutions on the market.
Check more information about our latest security products.
References
Anti Malware Mac
- https://www.macworld.co.uk/feature/mac-software/mac-viruses-list-3668354/
- https://macpaw.com/how-to/known-mac-viruses-malware-security-flaws
- http://factmyth.com/factoids/apple-macs-cant-get-viruses-or-malware/
- https://www.businessinsider.com/apple-mac-vs-windows-pc-why-i-chose-macbook-2018-3?op=1
- https://www.iphonelife.com/content/can-iphones-get-viruses-how-to-detect-remove-malware-viruses-your-iphone
- https://gigaom.com/2005/06/24/viruses-on-mac-os-x/
- https://www.businessinsider.com/how-to-get-rid-of-virus-on-mac?op=1
- https://www.computerhope.com/issues/ch000737.htm
- https://www.digitaltrends.com/computing/does-your-mac-need-antivirus/
- https://www.macworld.co.uk/feature/mac/security-firewall-3643100/
- https://www.enigmasoftware.com/cookieminer-removal/
- https://macdailynews.com/2019/01/31/new-cookieminer-macos-malware-swipes-your-cookies-to-steal-your-cryptocurrency/
- https://9to5mac.com/2019/01/31/cookieminer/
- https://www.pcrisk.com/removal-guides/14414-cookieminer-malware-mac
- https://blog.checkpoint.com/2017/04/27/osx-malware-catching-wants-read-https-traffic/
- https://www.intego.com/mac-security-blog/new-osxshlayer-malware-variant-found-using-a-dirty-new-trick/
- https://www.howtogeek.com/171993/macros-explained-why-microsoft-office-files-can-be-dangerous/
- https://www.myantispyware.com/2018/05/18/how-to-remove-mshelper-malware-from-mac-virus-removal-guide/
- https://lifehacker.com/how-to-deal-with-mshelper-the-latest-mac-malware-1826142837
Nowadays, Macs are part of the work-from-home workforce during the COVID-19 pandemic. If you've brought a Mac from the office to home, it's likely your IT department has already set it up to meet your company's security policies. But what if you're enlisting a Mac already at home to do duty for your company? You need to outfit it for business, to protect it and your company from infections and snooping, while ensuring it continues to run smoothly over time.
Guard Your Mac Against Malware Windows 10
Here are 21 tips for staying secure, private, and productive while working from home on your Mac—while also making sure your personal 'helpdesk' is in place, should you run into problems while doing your work.
How to guard against viruses and cyber threats on your Mac
While good security habits are important for all Mac users (since, contrary to popular opinion, Macs are as vulnerable to malicious attacks as PCs), you need to take special care when working from home on your Mac because you'll be interacting with your company's applications and platforms over the internet. Start your 'security upgrade' with the Mac itself, to keep it free of viruses and malware. Make sure your security checklist includes the following:
|
Trend Micro Mac Endpoint Security solutions include:
|
How to guard your privacy on Mac
Next, you need to make sure your work remains private. This means creating a 'chain of privacy' that extends from your Mac over the internet to your company's servers, so that each link in the chain is 'locked' to ensure your company data remains private.
|
Trend Micro Mac Privacy/Security solutions include:
|
Tips and tricks to maximize your Mac
Working from home means contending with home distractions (though working in the office has its own set of distractions too). Staying productive therefore includes setting good work and break habits, physically optimizing your work-from-home Mac setup, and keeping your Mac in good working order. Effective and productive remote working, when it comes setting up good work habits, using efficiency maximizing tools, and separating work from home activities, is a whole topic in itself. Here we include only those tips that directly affect the healthy operation and optimization of your Mac:
|
Trend Micro Performance tools include:
|
How to get remote computer assistance for your Mac
Finally, should things go wrong at any time with your working Mac setup, you need to make sure to have a work-from-home 'Help Desk' in place for when you need it. Download new itunes for mac. This can include the following:
|
Trend Micro Solutions include:
|
That's it! These tips should get you started on the road to staying secure, private, and productive, while running smoothly, as you work from home on your Mac. During the COVID-19 pandemic, many of us are doing just that. Now is the time to keep your working Mac working for you!

